Cambodia under attack
In 2012, the Cambodian government announced that it was in the process of drafting a Cybercrime Law which sparked fears that it could extend traditional media restraint to the online world. After the announcement, a hacker group called NullCrew launched a campaign named “Operation The Pirate Bay (OpTPB)” to attack Cambodian websites to protest against internet censorship and the arrest of Gottfrid Svartholm Warg, the 27-years-old co-founder of torrent sharing site The Pirate Bay. OpTPB targeted several websites of Cambodian businesses and government organizations, including the armed forces. As result, the operation leaked highly confidential information and posted a number of passwords for other hacktivist groups to use. Another hacktivist collective, Anonymous, caused over 5,000 documents to be stolen and leaked from Cambodia’s Ministry of Foreign Affairs. Following the above incidents, the Cambodian government announced a new law requiring surveillance cameras in internet cafes and telephone centers, and to retain footage for at least three months.
Article 28 of the draft law regulates user content and websites. People who “establish contents deemed to hinder the sovereignty and integrity of the country or government agencies and ministries, incite or instigate, generate insecurity and political [incohesion], and damage the moral and cultural values, etc. are punishable from one to three years imprisonment and fine from five hundred U.S. dollars to one thousand and five hundred U.S. dollars ($500-1500)”. Before Cambodia’s 2018 general election, a Chinese hacking group called TEMP.Periscope had shown extensive interest in the country’s politics, causing active compromises of multiple Cambodian entities related to the Country’s electoral system such as Cambodia’s National Election Committee, foreign affairs, interior and ministry of finance and senate. FireEye said it had been tracking the group’s activities since 2013 and believed that hackers were acting on behalf of the Chinese government in order to provide the Chinese government with widespread visibility into Cambodian elections and government operations. However, China denied supporting hacking attacks and said that they would not allow any individual to use any resources to commit cyber attacks.
ICT development in Cambodia is still at a sensitive stage compared to other countries in the region, and thus the country may be less prepared than others in terms of cybersecurity. The National Cambodia Computer Emergency Response Team (CamCERT) was established in December 2007 in order to deal with cybersecurity and cybercrime matters. There is also a Cybercrime Unit in the National Police department in charge of telecommunication crime. However, the country scores poorly in various categories of cybersecurity according to the Cyber-wellness profile published by the International Telecommunication Union (ITU) in 2014. Cyber-wellness in Cambodia has been discussed in a small circle among scholars because it seems to be a new topic in the country.
This research looks at Cambodia’s efforts in combating cybercrime, specifically trying to answer two questions: What are the main components of Cambodia’s cybersecurity policy and how was it developed? Does the draft law on cybercrime address cybersecurity issues in Cambodia, and is it balanced and in line with international cybersecurity standards? This research also aims to propose international good practices and concrete steps that the government of Cambodia may consider implementing.
Understanding Cybersecurity
Cybersecurity and law
The term “cybersecurity” was first used by computer scientists in the early 1990s in the context of networked computers. The term gained more widespread use, beyond a mere technical conception, when threats started to arise in the digital cyberspace. Cybersecurity has been defined by the ITU as “the collection of tools, policies, security concepts, security safeguards, guidelines, risk management
approaches, action, training, best practices, assurance and technologies that can be used to protect the cyber environment and organization and user's assets” or as “the prevention of damage to, unauthorized use of, exploitation of, and the restoration of electronic information and communication systems, and the information they contain, in order to strengthen the confidentiality, integrity and availability of these systems”. New technologies give rise to new trends in cyberspace crime. Their economic loss is estimated to exceed that of global drug trafficking. Some now consider global cybercrime the biggest underworld industry causing US$1 trillion loss worldwide annually.
In light of these developments, the gap between law and technology has widened. Traditional legal systems have failed to keep pace with new technology and ICTs that have made the impossible possible. The evolution of computers and information systems has given rise to new controversies regarding the boundaries and obligations, intellectual property rights, privacy rights, diplomatic relations and military affairs, critical infrastructure and, finally, public welfare. Cybercrime is one of the most serious threats to economic and national security around the world. The volume of data breaches, mostly caused by hacking and malware, is at the highest level ever. Highly confidential information is stolen and leaked causing significant legal and ethical concerns. Cybercrime can be defined as “any illegal behavior directed by means of electronic operations that target the security of computer systems and the data processed by them”. On the other hand, the term can be described as “computer-related acts for personal or financial gain or harm, including forms of identity-related crime and computer content-related acts”.Cybersecurity Actors
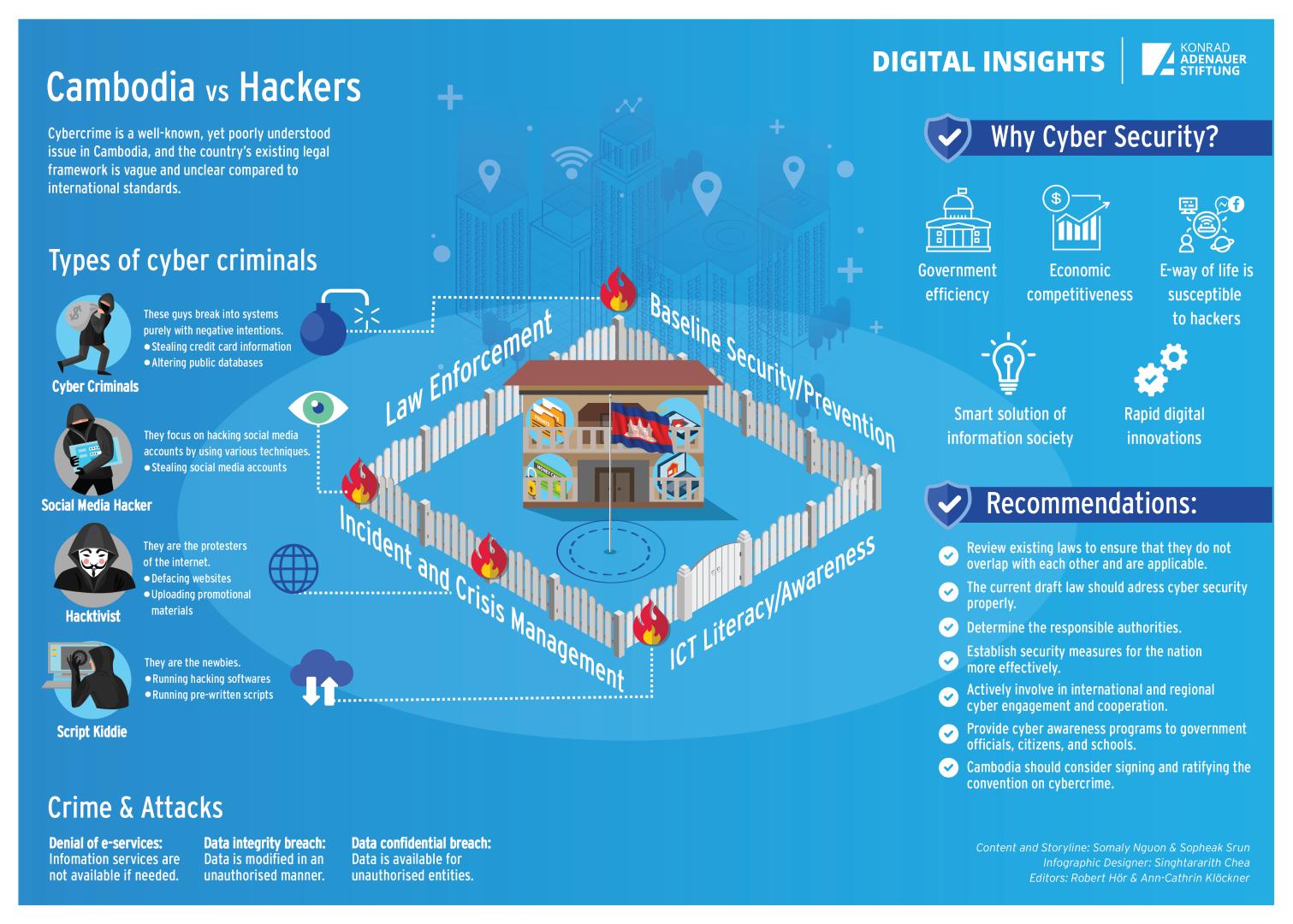
There are multiple actors perceived to be threats in the cyberspace, each with different behaviors and motivations behind their attack. According to Alexander Klimburg, cybersecurity actors are divided into three major groups includes: State Actors, Organized Non-State Actors, and Non-Organized Non-State Actors. Hacking without permission and authorization is considered illegal. But people usually have misconceptions about the term “hacker”, who according to Gross, “is anybody looking to manipulate technology to do something other than its original purpose”. Given the number of high profile data theft, severe compromises and stolen passwords, it is easy to see how the public forms negative opinions and assumes that all hackers have malicious intent. Nevertheless, there are some people who appreciate hackers as highly skilled computer experts who manipulate systems and expose vulnerabilities and point out flaws before really malicious actors can exploit them. Hackers’ actions inspire computer programmers to code their software more securely against vulnerabilities. Hence, hackers are categorized into several types, too.
For example, a “Script Kiddie” is a less experienced intruder who uses relatively simple programs written by expert hackers, thus automating all the difficult steps for them. A Script Kiddie usually cannot cause much damage due to their beginner level skills. A “Hacktivist” describes someone who uses computer skills to make political statements and actions. Social justice campaigners can deploy a range of hacktivist strategies to further their cause.[5] Famous examples of hacktivists working in groups include Anonymous, LulzSec or AntiSec. “Cybercriminals” use technology to facilitate a crime, primarily to gain money and personal benefit. Their targets could be anyone, from individuals to small businesses to large enterprises and banks. Cybercriminals attack by using social engineering tricks to manipulate users into providing sensitive information, steal their banking credentials, infect organizations, health care records or credit cards with ransom ware or another form or malware, and to exploit any weakness in the network. “Insiders” are hackers who are typically an employee, a former employee or a contractor who tries to steal sensitive documents or disrupt the organization’s operations. Edward Snowden is a prime example of an insider who hacked his own organization. Employees of an organization know exactly where precious information is stored. Last but not least, “state sponsored” actors are known as advanced persistent threats that consist of talented, well-equipped, well-organized and resourceful cyber attackers with advanced cyberattack tools, who work for a government in order to disrupt or compromise other governments, organizations or individuals in order to gain access to valuable data or intelligence, and can create incidents that have international significance.Categories of Cybercrime
Many different types of cybercrimes are committed every day on the internet, such as financial crimes, unauthorized access, theft, viruses/worms, Distributed Denial of Service (DDoS) attacks, trojan horse attacks, web jacking, cyber terrorism, cyber pornography, online gambling, IP crimes, email spoofing, cyber defamation, cyber stalking, etc.
In Cambodia, internet cafés have been an easy place for viruses to spread due to their limited cyber security measures. Other common issues reported in the country are web defacement, phishing, hacking, email hijacking, telecom fraud and fraudulent money transfer. The most targeted sites by hackers are government websites such those of ministries, government agencies and other high-ranking government officials. They are usually subjected to SQL injection and DDoS attacks. The Cambodian government experienced attack from groups such as Black Hats Team from Iran, Anonymous, Young Geek, Brothers Team and NullCrew, as mentioned earlier. Very few official reports are made about cyberattacks that target private companies offering online services, such as banks and telecommunication operators. The private sector and ISPs usually have better equipment and technical experts to monitor the network traffic, filter spam and defend against certain malicious acts in the cyberspace. Nevertheless, most cybercrimes and -attacks have gone unnoticed and most victims of cyber incidents are reluctant to report them. The low amount of incident reports may be either due to the low impact of the incidents or due to the limited legal procedures and enforcement.
Threat Responses
According to Soafer and Goodman, a significant weakness in the current system of combating computer misuse is the inconsistency between individual states of laws and effective investigation and prosecution measures. The ITU Global Cybersecurity Agenda (GCA) calls for strategies to develop cybercrime legislation that is globally applicable and interoperable with existing national and regional legislative measures, as well as to organize national cybersecurity efforts. The adoption by all countries of appropriate legislation against the misuse of ICTs for criminal or other purposes, including activities intended to affect the integrity of national critical information infrastructures, is central to achieving global cybersecurity. Since cyber threats can originate anywhere around the globe, the challenges are inherently international in scope and require international cooperation, investigative assistance and common substantive and procedural provisions. Thus, it is important that countries harmonize their legal frameworks to combat cybercrime and facilitate cooperation.
However, it can take time to update national criminal law and facilitate the prosecution of new forms of online cybercrime. Indeed, some countries have not yet gone through this adjustment process.[3] Cambodia does not have any specific legislation dealing with cybercrimes yet, although the new Cybercrime Law is being drafted and the Criminal Code 2009 takes care of the cybercrime issues.
How Cambodia Defines Cybercrime
There are different names for cybercrime law in different legal systems. For example, it is called “Computer Misuse Act” in Singapore. China got its “Cybersecurity Law” after The Standing Committee of China’s legislature passed it in November 2016. As of mid-2019 more Cambodians gain access to the internet, and the current “Cybercrime Law” is still in the drafting process. However, computer related offences were introduced for the first time in the Cambodian Criminal Code 2009 in Articles 317-320 and 427-432. The Criminal Code uses very general terms such as “Offences in information technology sector”.
There is no specific definition of cyber offense or the specific categories of cybercrime in this legislation, so the Criminal Code alone cannot secure the nation from cyber threats and impose appropriate punishment on cyber criminals. The challenge for Cambodia’s legal system is to stop the potential abuse of new technologies and make necessary amendments to the national criminal law.
Interestingly, some legal systems do not criminalize accessing another computer itself, unless the perpetrator has harmful intentions to obtain, modify, and damage the accessed data. Opponents to the criminalization of access refer to situations where no dangers were created by mere intrusion, or where acts of “hacking” have led to the detection of loopholes and weakness in the security of the targeted computer systems. In order to keep pace with innovation, the Cambodian government is putting more effort into legislating this space more appropriately.Legislating Cyberspace
This section analyzes the existing legal framework and mechanisms that address cybersecurity in Cambodia, in particular the Criminal Code 2009, the Press Law, the Telecommunications Law 2015 as well as the new draft Cybercrime law, looking at whether these laws sufficiently address cybersecurity issues or not.
Criminal Code of the Kingdom of Cambodia (2009)
The term “cybercrime” does not exist in any specific legislation in the Kingdom yet. While the controversial Cybercrime Law is still being drafted, the Cambodian Criminal Code 2009 has jurisdiction over the current cybercrime issues. Computer related offences were introduced for the time being in the Cambodian Criminal Code 2009 in Articles 317-320 and 427-432, the crimes being called “Infringement on the secrecy of correspondence and telecommunication” and “Offences in the information technology sector”. “Defamation and Insult” is considered a type of cybercrime as well, if committed via computer networks.
Infringement on the secrecy of correspondence and telecommunication – the right to correspond is an international fundamental right part of private life recognized under international human rights law and also applied to the secrecy of telecommunication. This right protects parties from any active interference; any censorship or other kind of active limitation on the free flow of communication is considered an interference and violation of the above rights. According to the Cambodian Criminal Code, any act of opening, disappearing, delaying or diverting the correspondence addressed to a third party, in bad faith, is an infringement on correspondence. In addition, fraudulently acquiring knowledge of the content of the correspondences addressed to a third party is categorized in the same way and is punishable by imprisonment of one to five years. Moreover, it can be fined between one hundred thousand and two million Riels. According Section 5 of this law, the act of listening or jamming a telephone conversation in bad faith shall be punishable in the same way. There are additional penalties as well depending on the category and duration of the act, such confiscation of materials, prohibiting against pursuing a profession, posting and broadcasting the decision of the sentence.
Offenses in the information technology sector – according to Article 427, the offenses refer to acts of having access to automated data processing or maintaining access and when the act has resulted in either deletion or modification of the data contained in the system. Also the act of obstructing the operation of automated data processing systems, fraudulent introduction, deletion or modification of data, participation in a group, or agreement to prepare for the commission of offences are considered offenses in the information technology sector. The phrase “having access to automated data processing or maintaining access” is being used in the current law without being specific as to whether it means illegal access, access to unauthorized data or intentional access to unauthorized data. The lawalso fails to specify the technical means and level of access and usage.
Defamation and insult – these are considered a type of cybercrimes as well if committed via computer network. Defamation is a concerning issue on the internet, defined as “an intentionally false communication, either published or publicly spoken, that injures another’s reputation or good name, or holds a person up to ridicule, scorn, or contempt in a respectable and considerable part of the community”. Article 305 of the Criminal Code defines defamation as “any allegation or slanderous charge that undermines the honor or the reputation of a person or an institution”. Defamation can be committed in the following ways: through speeches, announced in a public place or in a public meeting; in writing or sketches by any means whatsoever circulated in public or exposed to sight of the public; or by any means of audio-visual communication intended for the public.
In February 2018, the National Assembly and Senate approved amendments to the Criminal Code, introducing a new lèse-majesté offense (Article 437) that makes it illegal to defame, insult or threaten the king. It carries a sentence of one to five years in jail, and a fine two to ten million riel (about USD$500 to USD$2,500). In May 2018, the Ministry of Information warned media outlets of the law, saying that distributing or reposting material that insult the king, in print, online or otherwise, constitutes a lèse-majesté offense. Defamation and insult offenses under the Criminal Code are used together with the Press Law 1995. According to Article 306 and 308 of the Criminal Code, defamation and insults committed by means of media is subjected to the provision of the press law. The Press Law also restricts journalists from publishing information that harms someone’s honor and dignity and may be used to punish journalists who criticize public figures. It also imposes restrictions on content which “may affect the public order by inciting directly one or more persons to commit violence” or which “may affect national security and political stability” or which affects “the good custom of society”.Law on Telecommunications 2015
The Law on Telecommunications was promulgated in December 2015 as a legal instrument to supervise the telecom sector in Cambodia. The objectives of this law are to define the authority of the Ministry of Post and Telecommunication (MPTC), to establish and outline the duties of the Telecom Regulator Cambodia (TRC), to classify different types of authorization, certificate and licenses, and to set the supervision on the use of infrastructure and network, the fees, the fair competition and the protection of consumers. A Report of the UN Special Rapporteur Rhona Smith on the situation of human rights in Cambodia submitted at the United Nations Human Rights Council highlighted concerns over the adoption of this law. She noted that “the law requires telecommunications companies to turn over certain data to the government upon request”. She also highlighted that the degree of compliance with international human rights law lies in the interpretation and application of the law by law enforcement and judicial official.
According to Article 6 the MPTC shall have the competence to control telecommunications and ICT service data, and all telecommunication operators shall provide their service user data to the MPTC. A 2015 Regulation on Cell Phone Data threatens suspensions and fines for mobile operators who do not register the identities of consumers. The regulation obliges companies to supply police with identification details of SIM card holders on request. The TRC spokesman Im Vutha said that SIM card registration would enable the government to monitor telecom operators' databases. Moreover, Article 97 allows secret surveillance of communications if conducted with the approval of the “legitimate authority”. Article 80 states that the “establishment, installation and utilization of equipment in the telecommunications sector, if these acts lead to national insecurity, shall be punished by sentences from seven to fifteen years imprisonment.” In addition to imprisonment, the offender shall be fined from 140 to 300 million Riels. This could broadly mean that any communication conducted by any electronic means could be criminalized if it is deemed to create “national insecurity”.
It should be noted that in May 2018 the Cambodian government also issued an interministerial “Prakas” (or proclamation) which ordered all ISPs to install the software necessary to monitor, filter, and block “illegal” content, including social media accounts. The Prakas ordered the MPTC to “block or close” websites and social media pages containing content deemed discriminatory or posing a threat to national security or unity.
Article 66 provides for the general prohibition of any action in the communication sector that may “affect public order and lead to national insecurity”. Because of the unclear wording, individuals may find it hard to understand when it may apply, or when the consequences of their actions may constitute as a violation to this law, and thus incur penalties.
The law also provides specific powers for the destruction of evidence. Article 76 states that, “in case the evidence of this offense is prohibited products or dangerous, telecommunication inspection officials have the right to request the prosecutor’s ruling to destroy in line with applicable procedures”. It is unclear what the terms “applicable procedures” and “prohibited or dangerous products” mean. Destruction of evidence under this article could affect the right to fair trial for those charged under this law because if a defendant is deprived of material evidence, they are deprived of the fundamental right to a fair trial because they cannot present a complete defense.
The New Draft Law on Cybercrime
Cybercrime can be categorized into three main categories: (1) Acts against confidentiality, integrity and availability of computer data or systems, which include illegal access to computer systems; illegal access, interception or acquisition of computer data; illegal interference with a computer system or computer data; production, distribution or possession of computer misuse tools; breach of privacy or data protection measures; (2) Computer related acts for personal or financial gain or harm, which are computer related fraud or forgery; computer related identity offences; computer related copyright or trademark offences; sending or controlling sending of spam; computer related acts causing personal harm; computer related solicitation or 'grooming' of children and; (3) Computer content related acts such as computer related acts involving hate speech; computer related production, distribution or possession of child pornography; and computer related acts in support of terrorism offences. This section will walk through the main components of the Cambodian draft law on Cybercrime and analyze its scope, structure, definitions and mechanisms to implement this law in the future. The main questions are: How does Cambodia define cybersecurity under this draft law? Is this law proportionate and address cybersecurity itself?
Purpose, Objective and Scope
According to the Council of Ministers spokesman Ek Tha, the draft of the Cybercrime Law is designed to “prevent any ill-willed people or bad-mood people from spreading false information and groundless information”. Article 1 of the draft law states that, “This law has a purpose to determine education, prevention measures and combat all kind of offenses commit with computer systems”.[2] Moreover, this law has the objective to “ensure the implementation of law, anti-cybercrime and combating all kinds of offenses commit with computer systems” and to “ensure safety and prevent all [illegitimate] interest in using and developing technology”.
Draft Cybercrime Law is divided into six main chapters. Chapter 1 is the general provision that covers the purpose, objective, scope, terms and definition of this law. Chapter 2 covers the establishment of a National Anti-Cybercrime Committee (NACC), its composition, duties, officials, budget and other details. Chapter 3 provides the procedures of dealing with cybercrime offences including investigation powers. Chapter 4 covers specific types of offences such as illegal access, data espionage, illegal interception, and data interference. Chapter 5 covers the topics of mutual legal assistance, international cooperation and extradition. Chapter 6 is the final provision.
It should be noted that the NACC will be chaired by the prime minister, with the deputy prime minister also acting as deputy chairman, and include five secretaries of state from the Ministry of Interior, the Ministry of Foreign Affairs, the Ministry of Information, the Ministry of Post and Telecommunications and the Ministry of Justice. There will be one general commissioner from the National Police who will be included as member. Other members are representatives from Anti-terrorism, Council of Justice, Ecosoc, Chamber of Commerce and NiDA. The NACC will have the duty to create strategies, action plans and related programs in securing the cyber and information grid. It will advise and recommend courses of action to the General Secretariat of the National Anti-Cybercrime Committee, supervise workflows and implementations of the General Secretariat. Moreover, it will also issue findings and appropriate recommendations for ministries and departments to ensure the security of the cyber and information grid of the government, provides cyber and information grid security reports of the nation to the government and perform other duties directed by the government.
Offenses
Compared to the Cambodian Criminal Code 2009, new and more specific cyber offences are introduced in the draft law on Cybercrime such as illegal access, data espionage, illegal interception, unauthorized data transfer, and system interference. The unauthorized access to a computer system, interception made by technical means, alteration, deletion or deterioration of computer data shall carry sentences of six months to fifteen years imprisonment and fines between one million and twenty four million Riels.
Article 23 of the draft law introduces the offence of “illegal interception” of computer data. Interestingly, it resembles Article 3 of the Convention on Cybercrime, the international treaty adopted by the Council of Europe. However, unlike the European version, the Cambodian draft law fails to provide discretion of the criminalization based on “dishonest intent” or “in relation to a computer system that is connected to another computer system”.
The same issues remain in other offences of the draft law. The offences are defined in very broad terms and fail to make reference to malicious or fraudulent intent, considering that honest mistakes over the internet are likely to be caught and penalized. British charity Article 19’s Executive Director, Thomas Hughes, said, “With a version of the Draft Law released, the authorities can no longer deflect the legitimate concerns of the national and international human rights community”. Cambodia’s draft Cybercrime Law falls well below international standards on the rights for freedom of expression, information and privacy.
Investigating Cybercrimes and Collecting Digital Evidence
Gathering evidence is one of the main challenges in fighting cybercrime. Cybercrime is different from physical crime in terms of motives, intent and outcomes, but especially also in terms of evidence. As evidence arises out of an electronic discovery process, it is very important for the investigator to understand the capabilities of the cybercriminal suspects. Digital evidence can be destroyed during the discovery process, as it is typically made of binary data inscribed on a mass storage device and can contain executable code objects, images or other encrypted electronic content. Therefore, only computer forensic experts should conduct such investigations.
Article 17 of the daft law states that “for the purpose of gathering evidence, the expeditious preservation of the computer data or the data referring to data traffic, subject to the danger of the destruction or alteration, can be ordered by the prosecutor”. The law requires that service providers make user data available to the competent authorities under confidentiality conditions. Prosecutors are given significant powers to order the preservation of computer data or traffic data under the draft law, which may cause concern if a prosecutor is subject to political influence or lacks the necessary independence to balance the different interests involved, especially the protection of the right to privacy.
Therefore, it would be necessary to use the “Principle of Proportionality” and “Reasonable data management” during a cybercrime investigation, in order to guarantee that rights and safety are considered at equally.
While it is extremely important for a cybercrime investigator to understand the purposes, personalities and behaviors of the cybercriminals, and to use different analytical techniques with different types of digital evidence for a more effective result, policymakers and citizens should jointly discuss whether, in order to balance security and the right to privacy, ‘identity’ and ‘behavior’ should be regulated separately. There could be real additional dangers to citizens if extensive information on both ‘identity’ and ‘behavior’ is collected, as this data could be also exposed to malicious actors. Thus it would seem better for data collection efforts to focus on ‘behavior’ only.
Cybersecurity laws in China, Japan and Singapore
Governance, economy and society are important factors to consider when legislating cyberspace.
In 2013 a United Nations Working Group of Government Experts concluded that the UN Charter and international law are fully applicable to the state behavior in cyberspace, which has also been adopted by NATO countries. However, China does not fully agree that international law should have jurisdiction on the national cyberspace. China holds the view that each state should have the right to set its own rules. With a strong belief in “cyber sovereignty”, China, together with Russia and some other Asian countries, introduced its alternative position through the Shanghai Cooperation Organization (SCO) in the UN General Assembly.
China has been actively participating in high level dialogues and has signed several agreements for the purpose of protecting and improving cybersecurity. Yet, several of its national policies give extensive jurisdiction to the Chinese government to control cyberspace in areas of society and economy as well. The new Chinese Cybersecurity Law continues to enforce self-censorship on content and control over personal and business data. Therefore, the principle of international law that covers cyberspace and fundamental human rights is not being fulfilled in China.
In Japan, although freedom of expression, access to information and the right to privacy are arguably still practiced in a limited way, the country is a good role model in the fight against cybersecurity issues, notably in terms of public-private partnerships and effective international cooperation.
Japan launched its new Cybersecurity Strategy Plan in September 2015. It highlights the role of industry and civil society in maintaining Japan’s cybersecurity and the centrality of two-way information sharing. The Cybersecurity Strategic Headquarters functions as the command and control body to promote the plan, and the National Information Security Center (NISC) takes the lead in promoting cybersecurity policies set forth in this strategy.
Interestingly, the NISC is allowed to monitor government-affiliated agencies for the first time. The Japanese government adopted the Cybersecurity Basic Act in November 2014 and amended it in April 2016 in response to the Japan Pension Service hack to give the NICS new powers to monitor and audit the security of entities created by direct government approval or laws.
Japan is also a member of the Global Forum on Cyber Expertise and has been a member of two UNGGEs. The country is actively involved in high level international political dialogues and has a strong Asia-Pacific engagement program, working closely with ASEAN countries. JPCERT/CC, Japan’s national Computer Emergency Response Team Coordination Center (CERT/CC), was established in 1996 in order to work with government agencies, critical infrastructure operators, security vendors and civil society. It actively promotes collaboration and monitoring across the Asia-Pacific and enhances the sharing of threat information. It is also undertakes extensive capacity building across and outside the Asia-Pacific, and works with global partners on a Cyber Green Initiative, an effort to improve the general internet ecosystem health.
Singapore’s government created a new Cybersecurity Strategy Plan 2018 with the aim to establish a resilient cyber environment based on a strong infrastructure, a safer cyberspace and a vibrant ecosystem with international partnerships. Moreover, the Communication and Information Minister has promised to spend up to 10% of Singapore’s IT budget on boosting cybersecurity. In addition to this, an existing Computer Misuse and Cybersecurity Act was amended in April 2017, setting new standards for incident reporting, audits and risk assessment, such as dealing with personal information obtained via cybercrimes (e.g. hacked credit card details). Singapore also engages in a strong international program to establish itself as one of the region’s leading central government cybersecurity bodies. It has signed several MoUs with other ministries inside and outside the region. Singapore is active in forums such as the East Asia Summit, ASEAN cybercrime meetings and the ASEAN Regional Forum. The SingCERT, like the one in Japan, was established in 1997 and works to detect, resolve and prevent security-related incidents on the internet affecting Singaporean companies and users. SingCERT signed an MoU with India’s CERT-In to enable information sharing and incident response collaboration.
Conclusion and recommendations
Classifying different aspects of cybersecurity into manageable categories facilitates the development of national and international law governing the rights and duties of individuals and nations with respect to each category of activity. Cyberattacks can be categorized into three general categories: cybercrime, cyberterrorism and cyberwarfare. Cyberespionage is another separate concern connected to either state intelligence or hacktivism. This separation helps to address the shortcomings of present national and international legal frameworks in a more effective manner.
Cyberattacks largely defy the simple categorization of activity defined by existing laws, making it difficult for countries to apply the traditional definitions of crime, terrorism, warfare or espionage as understood under existing law. Traditional classifications break due to the aforementioned asymmetric nature of network communication.
The legal and legislative analyses of cybersecurity issues must distinguish not only between different cyber-threat actors such as nations-states, terrorist, criminals, and malicious hackers, but also between the different targets of cyberthreats. Such targets include critical infrastructure, which could lead to loss of life or significant damage to the economy, and intellectual property, which could affect a country’s long-term competitiveness.
Cambodia has made steady developments in the area of cyber policy and security. In order to strengthen the area of national telecommunication legislation, its government adopted the Law on Telecommunications in 2015 and launched its Telecom/ICT Development Policy in 2016. Other legislation such as e-commerce and cybercrime is in drafting process. Cambodia’s international cyber engagement is limited to engagement with ASEAN’s cyber discussion and bilateral engagement with Japan, South Korea and the United States. The engagement is focused on technical capacity building, and legislative and policy development assistance.
However, the existing legislation of Cambodia does not address cybersecurity well enough. Current criminal law provides a broad perspective of crime related to telecommunications without clear definitions of the types of crime. The offence of infringement on the secrecy of the correspondence and telecommunication, and offences in information technology sector are being used to address cybercrime in Cambodia during the absence of a specific Law on Cybercrime. Other legislations such as the Press Law and Ministry Prakas do not describe cybercrime appropriately. There are a number of good recommendations proposed by stakeholders and international partners that should be taken into consideration in order to improve cyber wellness in Cambodia.
The current draft law on Cybercrime needs to address cybersecurity issues based on specific classifications and characteristics of crime. The terms and definitions used in the draft law should be clear and accurate in order to prevent broad and vague interpretations or confusion among authorities, judicial bodies, law practitioners and stakeholders implementing the law. The law should at least reach the minimum international cybersecurity standard norms and practices.
For instance, the collection of digital evidence during the investigation should be handled by professional data forensics because digital data is fragile and can break easily. Moreover applying the principle of proportionality and reasonable data management during cybercrime investigation is necessary to avoid data and privacy violations.
Special training and capacity building conducted by experts is very important for effective cybercrime investigation, especially for law enforcement officials and others who work in government institutions.
Cambodia doesn’t need to establish an NACC, unless it is to become an independent body overseeing cybersecurity practices in terms of technical and general implementation.
The Cambodian government should also promote open discussion between government, public, private, civil societies and international partners when adopting any national legislations and policies, especially on ICTs and cybersecurity matters, because it involves multiple different aspects that are linked with long term development and competitiveness at local and international level.
In addition, the current legal framework concerning cybersecurity, such as the Criminal Code 2009, Press Law, Telecommunication Law 2015 and other relevant regulations, should be amended in terms of the provisions concerning the interpretation of crime itself and authority power, including those that provide unnecessary restriction and violations of fundamental rights. Cyber awareness programs should be implemented at all levels in order to help citizens become more aware of the potential risks and threats on the internet. The government should integrate such cyber awareness programs in school curricula because large numbers of young Cambodian are increasingly using the internet for various purposes without knowing about its dangers.
Last but not least, the government should increase its regional and international cooperation and partnerships in the field of cybersecurity. Cybercrime law will certainly play a major role in addressing cybersecurity in Cambodia, but it has to match international cybersecurity standards and comply with Cambodia’s legal oblations at all levels.
One major positive step would be for Cambodia to consider signing and ratifying the Convention on Cybercrime, also known as the Budapest Convention, the first international treaty seeking to address internet and computer crime by harmonizing different national laws, improving investigation techniques, and increasing cooperation among nations.
Even though the Convention on Cybercrime was adopted by the Committee of Ministers of the Council of Europe in 2001, as of March 2019, 63 states have already ratified the convention, including the United States, Canada, Australia, Japan, Philippines and Sri Lanka.
An effective, robust and balanced cybercrime law is important for Cambodia’s political, social and economic development, and therefore it will be in its best interests it to integrate best practices and effective measures from around the world.
The full publication inclusive sources can be found here.
Disclaimer
The designated contributions do not necessarily reflect the opinions and views of the editorial team and the Konrad-Adenauer-Stiftung. Hence, assumptions made in the articles are not reflective of any other entity other than the author(s) – and, since we are criticallythinking human beings, these views are always subject to change, revision and rethinking.